On Sep 24, 2014, a GNU Bash vulnerability with name of Shellshock or the “Bash Bug”, was disclosed. the vulnerability allows remote attackers to execut code given certain conditions by passing strings of code following environment variable assignments
You can find more details about the vulnerability on CVE-2014-6271 and CVE-2014-7169
Check System Vulnerability
On any system that is running bash you may check the ShellShock vulnerability by running the following command :
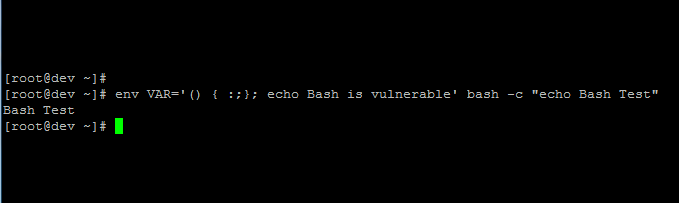
env VAR='() { :;}; echo Bash is vulnerable' bash -c "echo Bash Test"
“echo Bash is vulnerable” is where the remote attacker can inject malicious commands , if you see the following command your Bash is vulnerable and you need to update it .
Bash is vulnerable
Bash Test
Otherwise , if you’re not seeing “Bash is vulnerable” as output of command ,your version of bash is not vulnerable .
Fixing the vulnerability – Update Bash
It’s recommended to update your machines running Bash immediately , and check for updates and complete fix
– Debian / Ubuntu : APT-GET
sudo apt-get update && sudo apt-get install --only-upgrade bash
– Red Hat / CentOS / Fedora : YUM
sudo yum update bash
Don’t forget to check for the Shellshock again after the update !
Let me know if you have any question below on comments .
Ah , my machines was vulnerable . they’re updated now
Glad you patched it !