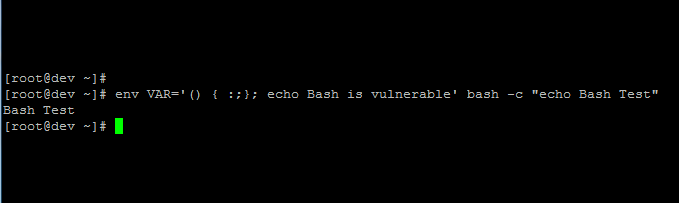
Hello All,
This is a note about the newest security vulnerability in Windows Servers with the access to Internet. This security bug allows the hacker to access your server remotely and install a backdoor on your windows servers. This is why we recommend all of the windows users to update their servers to the latest version and install the patches which are provided by Microsoft Website.
For more information, please go to the following website and read more about this bug.
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
Regards